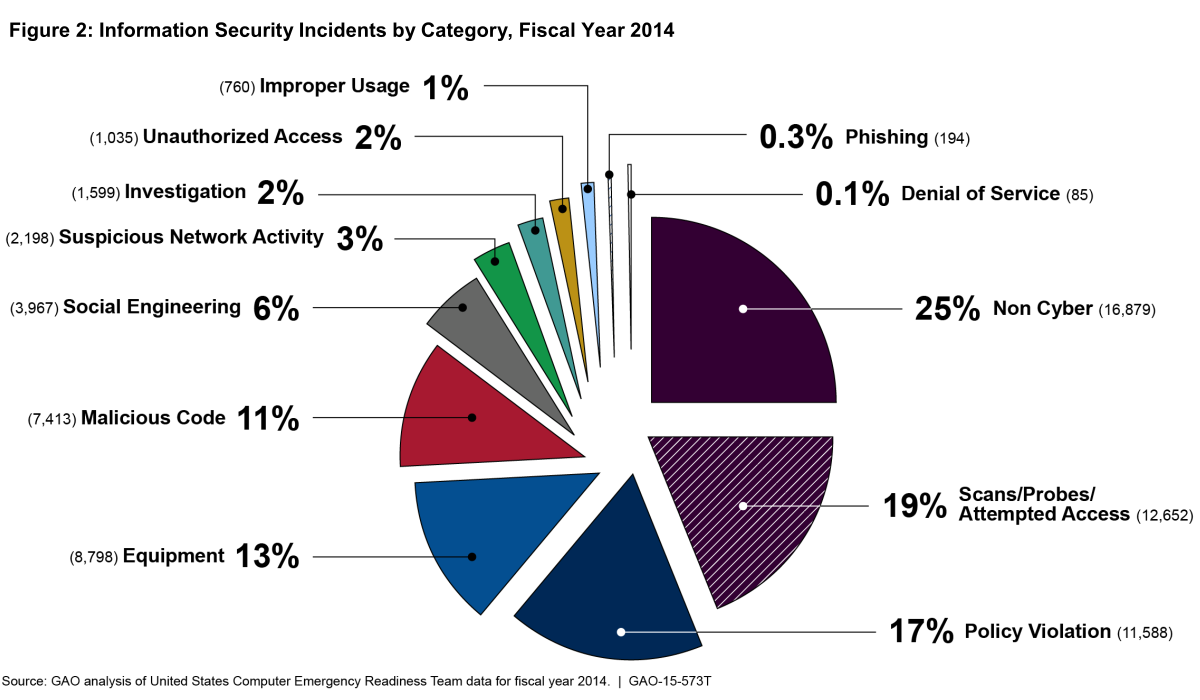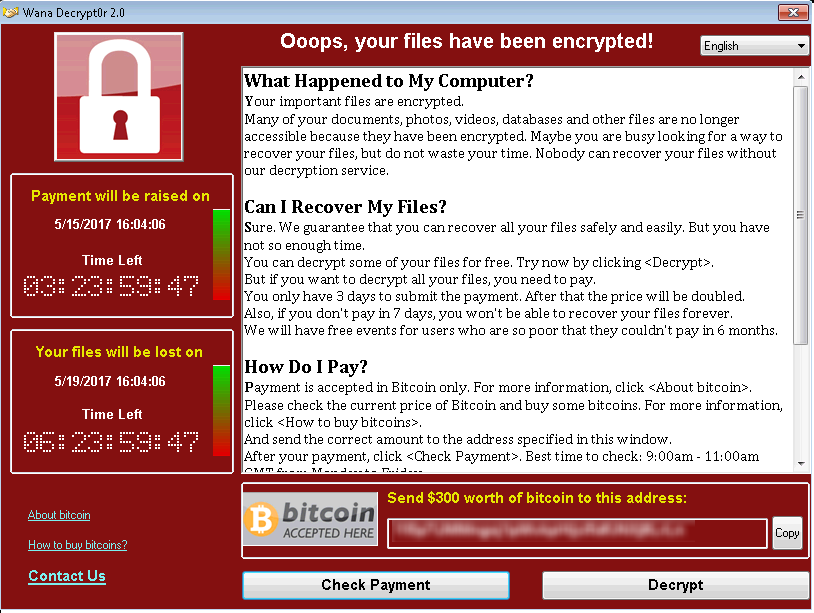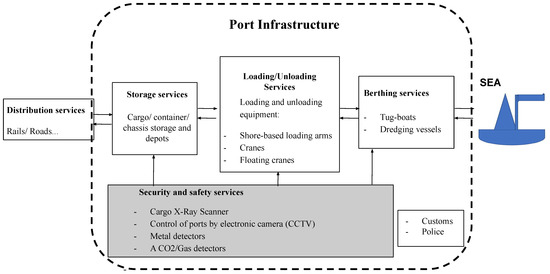
Information | Free Full-Text | Cyber Security in the Maritime Industry: A Systematic Survey of Recent Advances and Future Trends | HTML
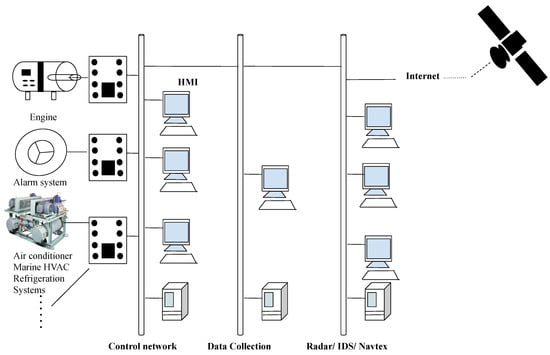
Information | Free Full-Text | Cyber Security in the Maritime Industry: A Systematic Survey of Recent Advances and Future Trends | HTML
Magniber ransomware being spread in the guise of a legit Microsoft Edge and Google Chrome update - NotebookCheck.net News
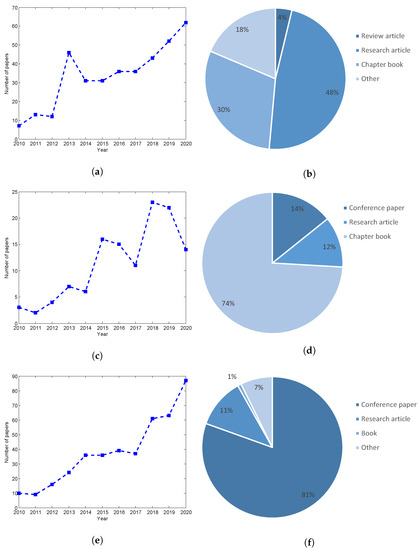
Information | Free Full-Text | Cyber Security in the Maritime Industry: A Systematic Survey of Recent Advances and Future Trends | HTML
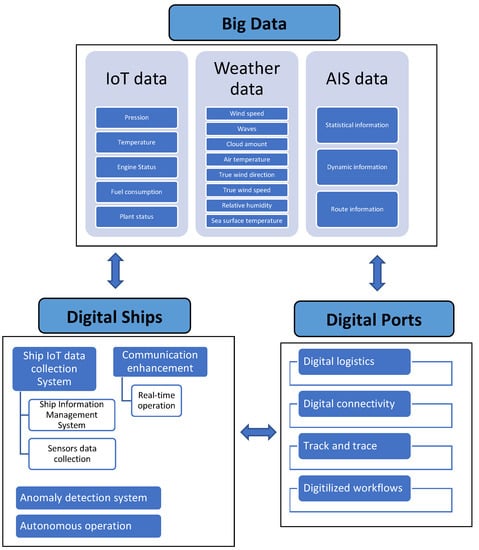
Information | Free Full-Text | Cyber Security in the Maritime Industry: A Systematic Survey of Recent Advances and Future Trends | HTML

Magniber ransomware being spread in the guise of a legit Microsoft Edge and Google Chrome update - NotebookCheck.net News